Staples (NASDAQ:SPLS), a well-known American office supply retailer, faced a cybersecurity breach that impacted its internal and customer-facing operations. The attack led to the shutdown of various internal operations, including backend processing and product delivery systems.
The company, which operates 994 stores across the US and Canada, along with 40 fulfillment centers, experienced severe operational disruptions. This situation was further compounded by reports of employees being unable to access essential services like Zendesk, VPN employee portals, and company email.
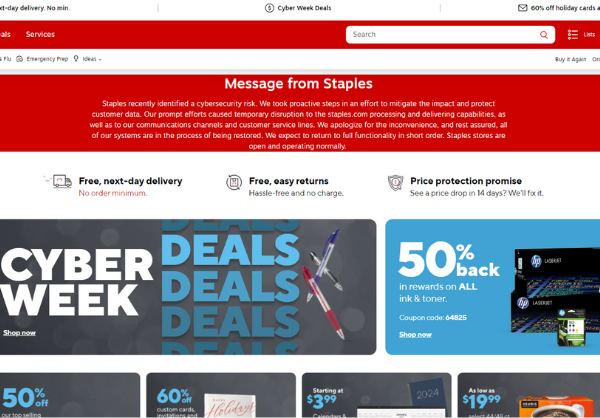
At the time of this writing, the company’s customer facing website staples.com is still unable to process orders.
Why it matters: This incident at Staples serves as a practical example for technology leaders of the challenges and responsibilities inherent in managing digital security. The company’s response to the cyberattack highlights the importance of having effective incident response strategies and the need for robust cybersecurity infrastructure to protect against such threats.
- The cyberattack on Staples, following a previous data breach in 2020, illustrates the ongoing challenges companies face in securing their networks against evolving cyber threats and serves as a reminder of the potential vulnerabilities in supply chain operations, emphasizing the need for comprehensive security measures across all aspects of business operations.
- The repercussions of the cyberattack extended beyond Staples’ internal operations, affecting its online platform and customer services. Despite the stores remaining operational, the company’s online order processing experienced significant delays, reflecting the widespread impact of the cyber incident.
- In response to the cyberattack, Staples implemented measures, including shutting down certain networks and systems. This action was part of an effort to contain the breach and safeguard customer data. A Staples spokesperson emphasized the company’s swift actions, noting the temporary disruptions to their processing, delivery capabilities, and customer service lines as a result.
- Despite no ransomware being deployed in the attack, the risk of data theft and subsequent extortion remains a concern, underscoring the need for continuous monitoring and advanced threat detection capabilities.






