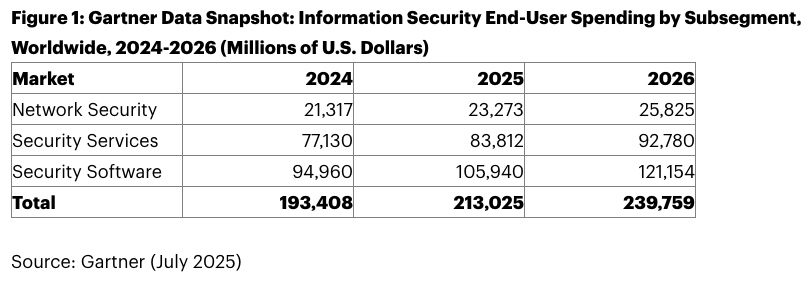
In a July 2025 press release, Gartner forecasted that global spending on information security and risk management will climb to $213 billion this year. These investments have less to do with any inflation or ongoing digital growth and are largely driven by the rising urgency around application security.
Risks have grown significantly as software environments and vulnerabilities develop with expanding attack surfaces, widespread use of third-party components, and increased reliance on AI.
Gartner’s accompanying report, Protect Software Supply Chains to Improve Application Security, offers a detailed look at what’s fueling some of this investment.
Software Supply Chains: Becoming the Battlegrounds
The research makes it clear that software supply chains are becoming the battlegrounds where modern cybersecurity threats materialize.
As enterprises become increasingly dependent on continuous integration and deployment, tools and systems used to build software have become prime targets.
Risks are harder to contain with vulnerabilities from compromised credentials to tampered code spanning across applications and stages of development. These changing threats are what’s fueling the forecasted investment and reshaping how organizations think about software trust.

The Three Components of Trust: Visibility, Integrity, Posture
While the forecast is forward-looking, Gartner’s supplemental research offers immediate direction for securing software supply chains around visibility, integrity, and posture.
- Visibility starts with knowing exactly what’s running in your environment. Organizations should focus on building a living inventory of their software assets, development pipelines, and third-party components. This means investing in tools that provide continuous insight with special attention to areas like open-source usage and artifact composition. Automated solutions such as Software Composition Analysis (SCA) and Application Security Posture Management (ASPM) tools can help teams move towards real-time oversight, offering a continuous view into the full scope of the software supply chain.
- Integrity goes a step further by proving that processes are secure, guaranteeing that software artifacts are trustworthy throughout development and delivery. Code should carry its own proof of origin, and changes should move through controlled, verifiable paths. The infrastructure supporting software builds must be protected in a way that makes tampering both difficult and detectable. Gartner specifically references a 2025 incident where a compromised GitHub Action leaked sensitive information, underscoring how fragile integrity must be enforced, rather than assumed.
- Posture refers to an organization’s ability to continuously evaluate and adapt the security state of its software supply chain. Controls are only effective if they’re actively monitored, and risks only matter if they’re understood in the context of the broader environment. It reflects the organization’s overall awareness of how secure its software supply chain is, and how quickly it can respond. Companies must treat security as a continuous cycle of assessment, response, and refinement where insights translate to action, and tools support decision-making teams.
The Expanding Threat Surface of AI and Open Source
The forecasted investment is also a hedge against the future.
AI integration is changing the shape of software, introducing new dependencies and creating more opaque development pipelines.
Organizations are now working with large language models, external datasets, and machine learning frameworks that don’t always offer the same transparency or control as traditional software.
As companies continue evolving their workflows and operations, automation and Gen AI are creating new threat surfaces.
For example, malicious actors may target AI models with poisoned datasets or vulnerable pre-trained libraries downloaded from public repositories. Additionally, the scale and speed of open-source adoption have led to a situation where 97% of modern applications contain OSS, with hundreds of components per app.
Compounding these risks is the rampant leakage of sensitive information often embedded in source code or exposed in public repositories.
GitHub reported 39 million leaked secrets in 2024 alone.
Addressing this requires a combination of management tools and security hygiene integrated directly into development workflows.
Regulatory Pressure and the Cost of Inaction
Security mandates are also shaping the urgency of investment and adoption.
Gartner’s research references multiple regulatory frameworks that now influence software supply chain expectations, including the U.S. Executive Orders 14028 and 14144, the EU Cyber Resilience Act (CRA), and the NIS2 Directive.
These initiatives emphasize accountability and transparency in software development, often requiring the generation and management of Software Bills of Materials (SBOMs) as a condition for doing business with governments or in regulated sectors.
Yet regulatory pressure alone cannot drive transformation.
One of the biggest challenges organizations face is the disconnect between security priorities and how work gets done, including:
- Cultural Resistance
- Fragmented ownership of CI/CD Infrastructure
- Inconsistent Team Alignment
The research advises starting with achievable milestones before expanding to more complex posture management or automated remediation initiatives.
A phased approach with stakeholder buy-in is critical to long-term success.
Trusted insights for technology leaders
Our readers are CIOs, CTOs, and senior IT executives who rely on The National CIO Review for smart, curated takes on the trends shaping the enterprise, from GenAI to cybersecurity and beyond.
Subscribe to our 4x a week newsletter to keep up with the insights that matter.
The Wrap
Gartner’s $213 billion forecast mirrors rising urgency.
Organizations are being asked to innovate and manage ecosystems, all while keeping their infrastructure, users, and reputations secure.
An organization’s integrity now depends on its foundational processes, with the software supply chain at the core.
The numbers speak for themselves. Companies understand that those who actively invest in blocking today’s threats will be the market leaders of tomorrow.