Cybersecurity has rapidly expanded in recent years, fueled by advancements in technology, heightened organizational preparedness, and a surge of new government regulations. This growth, however, is a direct response to the alarming increase in cyberattacks, which have become more frequent and sophisticated, forcing the industry to evolve at an unprecedented pace.
With the stakes higher than ever, technology leaders are laser-focused on the threats that could jeopardize their organizations. From the relentless pressure of ransomware to the elusive dangers posed by insider threats, these challenges demand immediate and sustained attention.
The National CIO Review, in collaboration with the CIO Professional Network, conducted an in-depth survey to uncover the cybersecurity issues that weigh most heavily on the minds of these executives. The results offer a snapshot of the most pressing threats organizations must address to safeguard their operations.
Ransomware Attacks
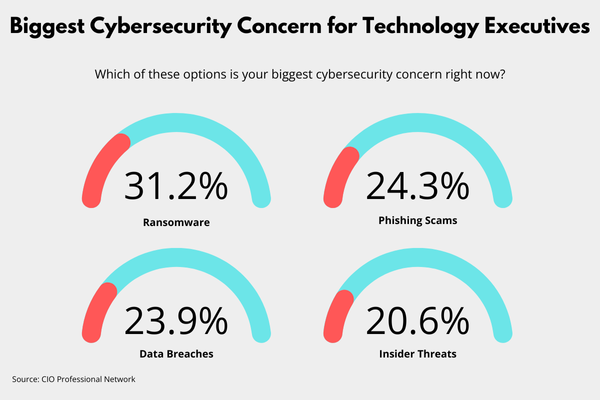
Ransomware has emerged as the most significant cybersecurity threat, capturing 31.16% of the survey votes from technology executives. While ransomware has been a persistent issue for years, 2024 has seen a dramatic spike in incidents, with a 27% increase in attacks compared to the previous year, according to research from The Thales Group.
These increasingly sophisticated attacks have affected various sectors, healthcare being particularly hard-hit. One notable incident in 2024 was the massive ransomware attack against Change Healthcare, which disrupted services for weeks, compromising sensitive patient data, and leaving millions of patients without access to critical medications.
The consequences of ransomware are severe, leading to substantial financial losses, reputational damage, and operational disruptions. Despite the escalating threat, many organizations remain ill-prepared, lacking a formal ransomware response plan, which leaves them vulnerable to extortion and data loss.
Phishing Scams
Phishing scams ranked second in the survey, receiving 24.32% of the votes, underscoring their role as a major entry point for cyberattacks. Attackers have increasingly refined their social engineering tactics, making it easier to trick individuals into divulging sensitive information.
According to the 2024 CrowdStrike Global Threat Report, identity-based attacks—often launched through phishing—have surged. Cybercriminals are now using advanced techniques such as SIM-swapping, bypassing multi-factor authentication (MFA), and exploiting stolen API keys to gain unauthorized access to critical data.
The rise of remote work has further amplified the phishing threat, as employees frequently connect to corporate networks from less secure environments. In response, organizations are ramping up their phishing awareness programs, implementing advanced email filtering technologies, and strengthening security with MFA to mitigate the risk of these increasingly sophisticated attacks.

Data Breaches
Data breaches, ranked as the third biggest concern with 23.97% of the survey votes, remain a formidable challenge for organizations. They have become alarmingly frequent, with reports of breaches affecting both large and small entities across various sectors. In the first half of 2024 alone, there were over 1,500 reported breaches, impacting more than 1 billion victims.
Human error remains a primary cause of these breaches, with misconfigurations and compliance failures playing a significant role. To combat this, organizations are placing a stronger emphasis on comprehensive cybersecurity training programs, ensuring employees are well-versed in the latest attack methods used by threat actors to steal sensitive data.
The consequences of data breaches are severe, both financially and reputationally. To mitigate these risks, companies are increasingly investing in stronger data protection strategies, including encryption, regular security audits, and strict adherence to compliance standards. Alongside technical measures, ongoing employee education is crucial in safeguarding against these pervasive threats.
Insider Threats
While external cyberattacks often dominate the headlines, CIOs and CISOs must also contend with the significant risks posed by insider threats, which garnered 20.55% of the votes in the survey, ranking fourth among cybersecurity concerns.
Insider threats, whether malicious or accidental, are particularly dangerous because they originate from trusted users and systems, making them difficult to detect. These threats can range from a disgruntled employee deliberately leaking sensitive data to an unwitting staff member accidentally exposing passwords or confidential information.
The challenge of managing insider threats is compounded by the fact that such actions often evade traditional detection systems. The rise of remote work and the use of personal devices for work purposes have further complicated this issue, demanding heightened vigilance from organizations.

In response, many companies have adopted a “zero trust” approach, which operates on the assumption that no one inside the network is inherently trustworthy. This strategy involves continuous monitoring, data segmentation, and the deployment of advanced security technologies. However, even with these measures in place, insider threats remain a formidable challenge, necessitating ongoing and proportionate strategies to protect against potential breaches.
The Wrap
Today’s digital threats loom larger than ever, and the insights drawn from this survey are not just data points – they are a resounding call to action.
As ransomware, phishing scams, data breaches, and insider threats continue to advance, they strike at the very heart of organizational security. The survey reveals that CIOs, CISOs, and technology leaders are not only aware of these dangers but are deeply concerned about the potential impact.
With the future of digital operations hanging in the balance, the stakes have never been higher, and the cost of inaction could be catastrophic. Now is the time to fortify defenses, or risk being left exposed in an increasingly hostile digital world.





