With cyber threats continually evolving at dizzying speeds, cybersecurity has emerged as a top priority for organizations across industries. The National CIO Review, in partnership with the CIO Professional Network, embarked on a joint survey initiative to discover the key focus areas that technology leaders believe are crucial for strengthening organizational resilience against cyber threats.
The survey, which gathered responses from a diverse range of professionals, provides valuable insights into the strategic priorities organizations are currently emphasizing to bolster their defenses. From enhancing identity and access management protocols to investing in employee training and awareness programs, the survey results underscore the multi-faceted approach required to combat the expanding array of cyber risks.
Notably, the findings also highlight a growing recognition of the need to adopt proactive measures, such as implementing advanced threat intelligence and analytics capabilities, to stay one step ahead of increasingly sophisticated and relentless adversaries. This survey shines a light on the key focus areas currently shaping the cybersecurity strategies of leading enterprises, offering a roadmap for technology leaders seeking to fortify their organizations against the looming threat of cyber attacks.
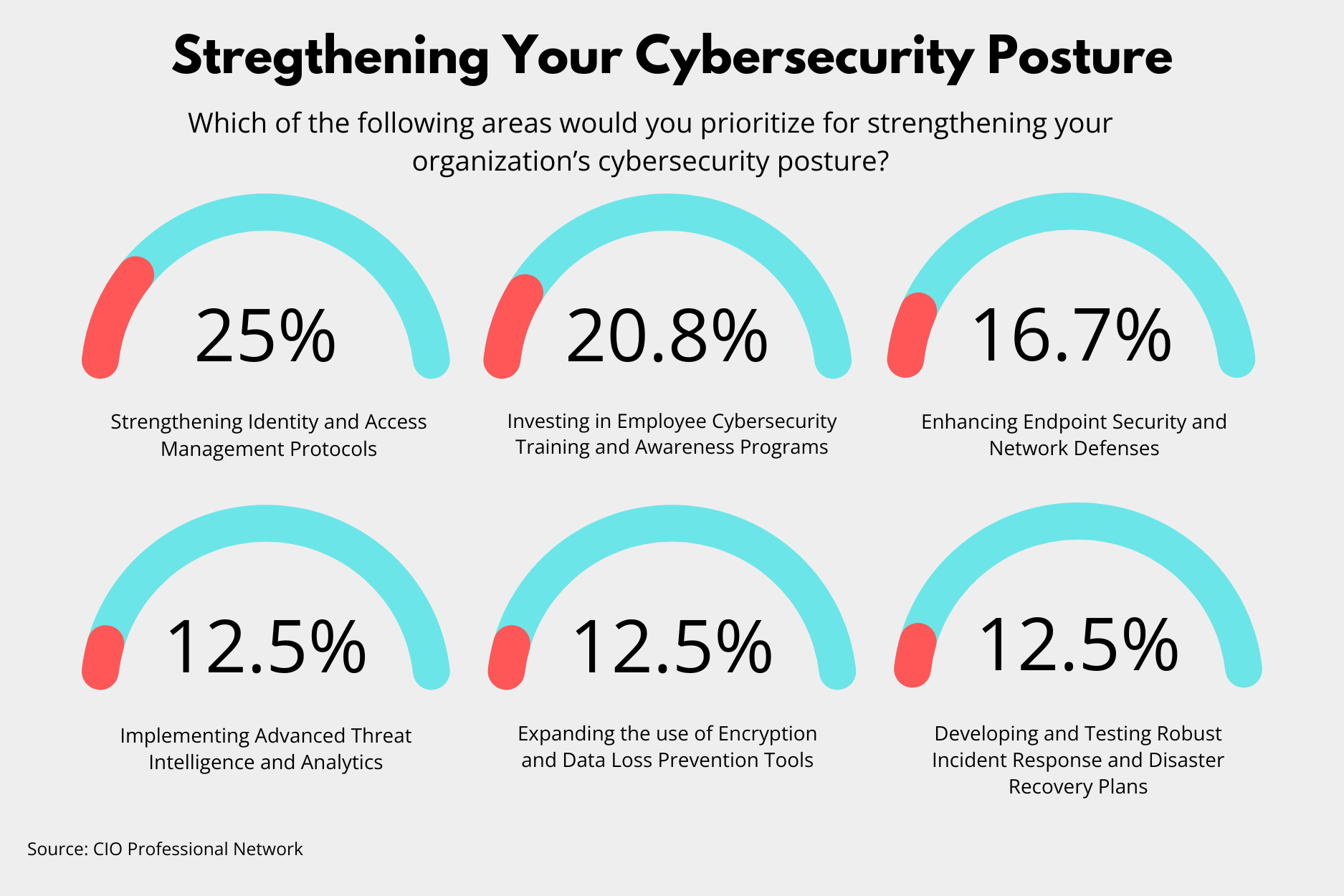
Strengthening Identity and Access Management (25%)
According to the survey, the highest priority is strengthening identity and access management protocols, which received 25% of the votes. In a time where data breaches and unauthorized access are increasingly common, leaders feel that strict identity and access management (IAM) systems have become indispensable.
They help ensure that only authorized individuals can access sensitive information and critical systems, effectively reducing the risk of insider threats and external breaches. Organizations have the potential to significantly enhance their security posture by implementing more stringent IAM protocols.
Investing in Employee Cybersecurity Training and Awareness Programs (20.83%)
Following closely behind IAM, investing in employee cybersecurity training and awareness programs was voted the second most crucial area, capturing 20.83% of responses. This result showcases the recognition that human error often plays a significant role in security breaches. Regular training and awareness programs can be vital in educating staff about the latest phishing schemes, malware attacks, and safe online practices.
Empowering employees with this knowledge fosters a security-friendly culture and also serves as a critical defense layer against cyber threats.
Enhancing Endpoint Security and Network Defenses (16.67%)
Enhancing endpoint security and network defenses ranked third, with 16.67% of the votes. As the number of endpoints within organizations grows due to the increasing use of mobile devices and the proliferation of IoT devices, securing these points becomes paramount. Strengthening endpoint security involves deploying advanced malware protection, conducting regular patches and updates, and monitoring networks for unusual activity that could indicate a breach.

Threat Intelligence, Encryption, and Incident Response Plans (12.50%)
Interestingly, areas such as implementing advanced threat intelligence and analytics, expanding the use of encryption and data loss prevention tools, and developing and testing robust incident response and disaster recovery plans each garnered 12.50% of votes. These survey results highlight a balanced concern across various aspects of cybersecurity, pointing to the need for a comprehensive approach that includes not only preventive measures but also capabilities to quickly respond and recover from incidents.
The emphasis on advanced threat intelligence and analytics indicates a shift towards proactive security measures, where organizations are keen on not just defending against known threats but also predicting and mitigating potential future attacks. Similarly, the focus on encryption and data loss prevention tools reflects an acute awareness of the importance of protecting data integrity and confidentiality.
Finally, the importance placed on developing and testing incident response and disaster recovery plans signifies an understanding that breaches are not just possible but likely. Being prepared to respond swiftly and effectively can minimize the impact of such incidents on operations and reputation.
The Wrap
Technology professionals have spoken, outlining a proactive and comprehensive framework necessary for bolstering their collective defenses. The prioritization of identity and access management protocols, combined with the critical need for employee education and robust endpoint security, forms a triad of essential strategies. Meanwhile, the equal weight given to threat intelligence, data protection tools, and resilient recovery plans underscores a holistic approach to cybersecurity, recognizing that a breach’s impact is not limited to the point of entry, but reverberates across the entire organization.
While the world of cybersecurity may be fraught with threats, remaining ahead of the curve can allow technology leaders to be well-equipped to safeguard the digital frontiers of tomorrow.






