The cybersecurity landscape in 2025 is defined by urgency and complexity in the face of relentless threat possibilities. As the frequency and sophistication of cyberattacks grow, organizations are learning that primed incident response (IR) capabilities are becoming business-critical.
To understand where security teams believe the most critical gaps lie, The National CIO Review, in conjunction with the CIO Professional Network, conducted a community poll asking technology leaders: “What are the biggest priorities for improving your cyber incident response?“
The findings reveal the mindsets of tech executives and how they plan to improve their incident response readiness.
Threat Detection & Log Analysis: Finding the Needle in the Haystack (27.27%)
Sharing the lead with 27.27% of the total votes, is threat detection and log analysis, as it remains one of the most foundational, yet persistently difficult, aspects of effective incident response.
Security teams today are inundated with data as logs from endpoints, applications, network infrastructure, and cloud services flood SIEM platforms around the clock. Yet, despite all this information, the most difficult part is finding meaningful insights hidden within.
Many teams suffer from alert fatigue, where genuine threats get buried under a mountain of false positives. Even advanced threat detection systems, when misconfigured or overwhelmed, can fail to surface the signals that matter most. The result is a dangerously delayed response, giving adversaries more time to expand and exfiltrate data.
Often, there’s also confusion around shared responsibility models between the organization and cloud providers.
Improving threat detection means smarter analysis, tighter integration between systems, and the ability to contextualize alerts within the broader threat landscape. Security leaders must invest in technologies prioritizing correlation and precision, along with personnel capable of interpreting data rapidly.
In a high-volume threat environment, clarity is what drives effective response.
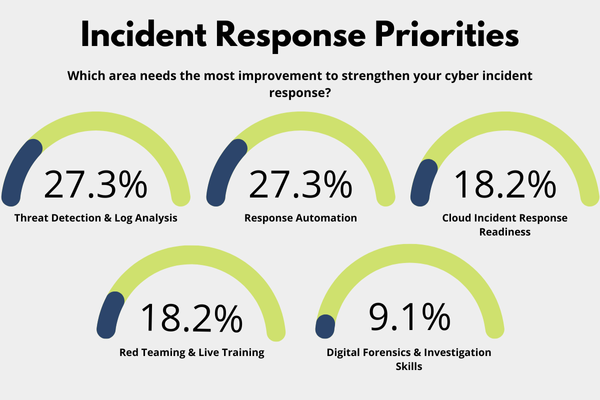
Response Automation: A Co-Leading Bottleneck (27.27%)
Tied for the top spot, response automation also received 27.27% of votes as a top priority for improvement.
In theory, automation holds the key to faster containment and improved consistency. Yet, in practice, many organizations are still in the early stages of adoption. Implementation challenges are widespread as intertwining automation platforms with legacy systems can be sophisticated and time-consuming.
Even when technically feasible, there’s often cultural hesitation to trust automation in high-stakes scenarios, particularly for actions like isolation or remediation. The concern may seem just about breaking things, but it really stems from accountability and confidence in the system’s decision-making logic.
Nonetheless, pressure to act quickly during an incident is immense as manual workflows can’t keep up with the speed of modern threats.
For organizations seeking to improve their IR programs in 2025, identifying where automation can create the most value is a vital next step.
Trust in automation will follow when results are demonstrable and measurable.
Cloud Incident Response Readiness: (18.18%)
Sharing second place with 18.18% of the total votes is cloud incident response readiness.
While organizational transitions to cloud-based environments unlock new realms of scalability and speed for enterprises, integrations have also introduced a new dimension of risk that many organizations are struggling to manage.
Traditional IR models built for on-premise infrastructures often falter within the dynamic and decentralized nature of cloud environments. Security teams face difficulties detecting misconfigurations, managing identity and access across services, and achieving visibility into cloud-native applications.
Often, there’s also confusion around shared responsibility models between the organization and cloud providers.
To close this gap, organizations must rethink their IR playbooks with cloud-specific scenarios in mind. Cloud integrations mean adapting to a fundamentally different environment where perimeter security is no longer a reliable concept. In 2025, building cloud security responses is becoming a prerequisite for cyber resilience.
Red Teaming & Live Training: Practice Under Pressure (18.18%)
Also earning 18.18% of responses, red teaming & live training is a priority for leaders who recognize that no playbook, however detailed, can substitute for real-time decision-making experience.
In the high-pressure environment of a live incident, team coordination can easily break down without practice.
Pressure-testing defenses can validate incident response protocols and uncover hidden weaknesses through exercises, such as tabletop scenarios or full-scale breach simulations, to ensure everyone knows their role when every second truly counts.
Despite its high value, red teaming is still underutilized due to the mandatory resources that can be hard to justify without a recent crisis.
However, its return on investment is significant. Teams that train together under realistic conditions are far more effective when facing a genuine breach. For CIOs, embedding red teaming and simulation exercises into the regular security calendar is imperative.
Digital Forensics & Investigation Skills: The Underestimated Capability (9.09%)
Though only 9.09% of respondents identified digital forensics & investigation skills as their top priority, this area’s importance remains particularly in the aftermath of an incident.
Forensics provides the extensive visibility needed to determine the cause and scope of impact. Without it, organizations may struggle to draw definitive conclusions, delaying recovery and impairing post-incident reporting. -While some organizations can effectively outsource forensic investigations, it can also hinder early-stage incident response and reduce internal awareness of threat patterns and vulnerabilities.
Even if an organization doesn’t maintain a full in-house forensics team, it benefits greatly from having core investigative skills embedded within the security function. This ability enables faster triage and more informed communication with third parties.
With regulatory and legal scrutiny around breaches continuing to rise, the ability to conduct thorough and defensible investigations remains at the forefront for a minority group of leaders.
The Wrap
TNCR’s community poll results present a compelling portrait of the modern cybersecurity leader’s mindset.
As organizations look to bolster their incident response capabilities, the focus is clearly shifting toward speed, precision, and preparedness. Automation and threat detection/log analysis sit at the heart of that strategy, helping teams respond faster and more intelligently.
Similar sentiments around cloud readiness and red teaming highlight the continuing battle and importance of preparing teams for emerging threats and proper reactions.
While digital forensics remains inherently valuable for effective communications and triage, its ability to be outsourced is leaving it outside the primary focus.
However, these priorities are not in competition.
Resilient organizations will seek each of these areas holistically, understanding that true incident response maturity is about the people and process as much as it is about the platforms and tools.
Moving deeper into 2025, CIOs and CISOs must lead with urgency, clarity, and a commitment to continuous improvement.
The threats will not slow down, but with the right investments, the response can outpace them.






