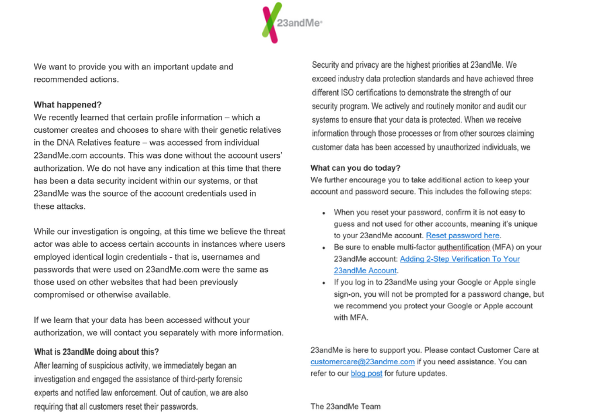
The recent security incident involving 23andMe, a popular genetic testing company, has raised concerns about the safety of personal and genetic data. The company sent out an email to its users, detailing the nature of the unauthorized access to certain accounts.
Interestingly, 23andMe has been clear that they don’t believe the issue originated from within their own systems. Instead, they’ve used this incident as an opportunity to educate users on the importance of robust security practices.
The Incident: Not an Internal Breach?
One of the most striking aspects of 23andMe’s communication about the incident is their assertion that there is no indication of a data security incident within their own systems. This is a significant point, as it shifts the focus from a potential vulnerability in 23andMe’s security infrastructure to the practices of the users themselves. The company believes that the unauthorized access occurred because users had identical login credentials across multiple platforms, some of which may have been compromised.
User Responsibility
While 23andMe is still investigating the incident, they’ve taken this as an opportunity to remind users of the importance of good security hygiene. They’ve not only initiated an investigation but also engaged third-party forensic experts and notified law enforcement. Moreover, they’ve required all users to reset their passwords as a precautionary measure.
The company goes on to remind it users that they’ve offered multi-factor authentication (MFA) since 2019 as an additional layer of security and stresses the need for unique, hard-to-guess passwords and the activation of MFA. For those using Google or Apple single sign-on, the company recommends enabling MFA on those accounts as well. In essence, 23andMe is using this incident to underscore the shared responsibility between service providers and users in maintaining data security.
The Wrap
It’s reassuring to some extent that 23andMe claims their internal systems were not the source of the unauthorized access. However, this also raises questions. By emphasizing user responsibility, are they subtly deflecting from a deeper issue that might exist within their platform?
For ongoing updates and assistance, 23andMe directs users to their Customer Care at customercare@23andme.com and to their blog posts for future updates. But this incident serves as a complex reminder that in the digital age, the lines between corporate responsibility and user vigilance are increasingly blurred.
It’s crucial for users to question and scrutinize the security measures of platforms they entrust with sensitive information, even as they take steps to protect themselves.






