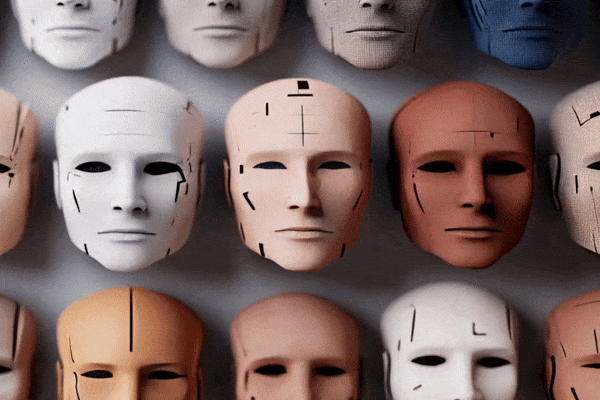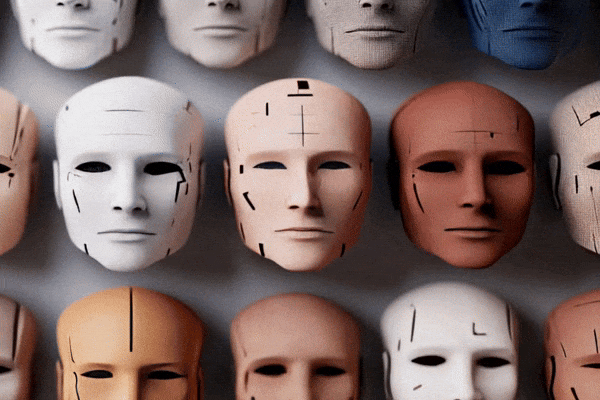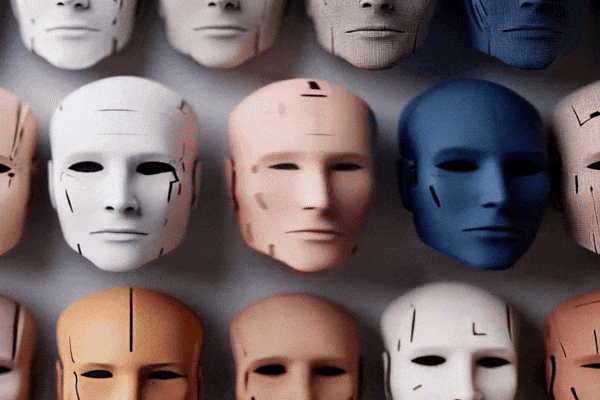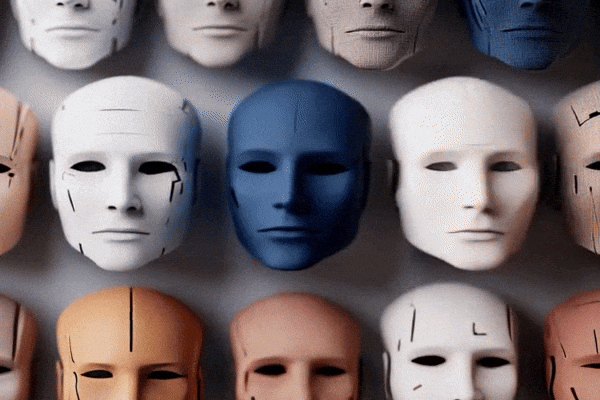
The idea of someone using deepfake technology or AI-generated identities to land a job might have once sounded like science fiction, but it’s now a documented reality. While these cases are still uncommon, the fact that they’re happening at all, particularly in remote hiring scenarios, should give companies pause. Fraudulent candidates have passed interviews, secured job offers, and in some cases, gained access to sensitive systems and data, all under false identities.
And most traditional hiring processes weren’t designed with this type of deception in mind.
In remote or hybrid settings, where interviews happen over video and documents are submitted digitally, it’s easier than ever to manipulate visual and auditory cues. A convincing voice-clone, a deepfaked video feed, or a fabricated resume crafted by generative AI can be enough to get through screening.
As companies increasingly embrace remote and global talent pools, understanding these threats and implementing strategies to identify and prevent such fraud is becoming an essential aspect of secure hiring.
Why It Matters: For Chief Information Officers (CIOs), Chief Information Security Officers (CISOs), and technology leaders, the emergence of fake candidates using advanced technologies represents a significant security vulnerability. In technical roles where employees have access to critical systems and sensitive data, the infiltration of a synthetic applicant can lead to espionage, data breaches, or ransomware attacks. Integrating stringent verification measures into the recruitment process is crucial to protect organizational assets and maintain trust.

- AI-Powered Deception Is Already Getting Past Screening: Fake candidates are successfully leveraging deepfake video, voice synthesis, and AI-written resumes to pass remote interviews. In one case, the cybersecurity firm Exabeam flagged a candidate for a GRC analyst role after noticing mismatched lip-syncing and synthetic voice cues during a live video call. The person had already cleared earlier rounds, proving how convincing these deceptions can be at first glance.
- State-Backed Fraud Rings Are Targeting the Tech Sector: U.S. officials have confirmed that North Korean operatives have been using false identities and deepfake technologies to secure remote jobs with American tech firms. In one instance, a North Korean agent was hired as a software engineer and used their access to conduct internal reconnaissance and divert income back to sanctioned entities. These individuals funneled earnings, totaling approximately $88 million over six years, back to the North Korean regime.
- Incidents Aren’t Limited to Small Companies or Unvetted Roles: HYPR, a New York-based identity security firm, uncovered a fake hire when the supposed candidate began missing onboarding meetings and failed to pass identity verification. Clues included location mismatches and refusal to appear on camera after being hired. KnowBe4, another cybersecurity company, similarly discovered a North Korean IT worker attempting to transmit unauthorized files upon receiving company hardware. These are well-resourced organizations with strong vetting processes, yet fake candidates still slipped through.
- Subtle Signs Are Often the Only Clues: Candidates who avoid video calls, use overly scripted responses, delay when answering technical questions, or exhibit voice anomalies could be using AI tools or relying on hidden support during interviews. Technical leaders must create protocols to spot these inconsistencies, such as unscheduled technical walkthroughs or cross-team video follow-ups.
- Hiring Needs to Be Treated Like Access Control:
Especially in IT and DevOps roles, candidates may receive privileged access within days of hire. If verification fails, the organization risks handing the keys to attackers. Technology leaders should advocate for multi-stage identity checks, use metadata analysis on applications, and implement short-term sandbox environments where new hires can be validated through real performance before being granted full access.
Go Deeper -> Detecting Fake Candidates – Vidoc Security Lab