One of the most significant challenges for organizations today is establishing cybersecurity measures that are both effective and legally defensible. Local and state governments often require the implementation of “reasonable cybersecurity” without providing a clear definition of what that entails.
This lack of a national standard for reasonable cybersecurity in the United States forces organizations to navigate a complex patchwork of state laws and industry standards.
The Center for Internet Security (CIS) recently released its “Reasonable Cybersecurity Guide,” offering a comprehensive framework to help organizations meet these challenges. This guide aims to protect organizations from cyber threats and, just as importantly, reduce their legal exposure by providing clear, actionable security practices.
Federal and State Cybersecurity Inconsistencies
Federal cybersecurity regulations in the United States are fragmented and sector-specific. Critical infrastructure entities, for instance, must report cyber incidents to the Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency.
In contrast, organizations in the financial services sector adhere to standards set by the Federal Financial Institutions Examination Council.
At the state level, nearly all states require breach notifications, forcing businesses to notify affected individuals via mail if a data breach occurs. States like California and New York have adopted comprehensive data privacy laws, which include specific cybersecurity requirements, setting a higher standard for data protection.
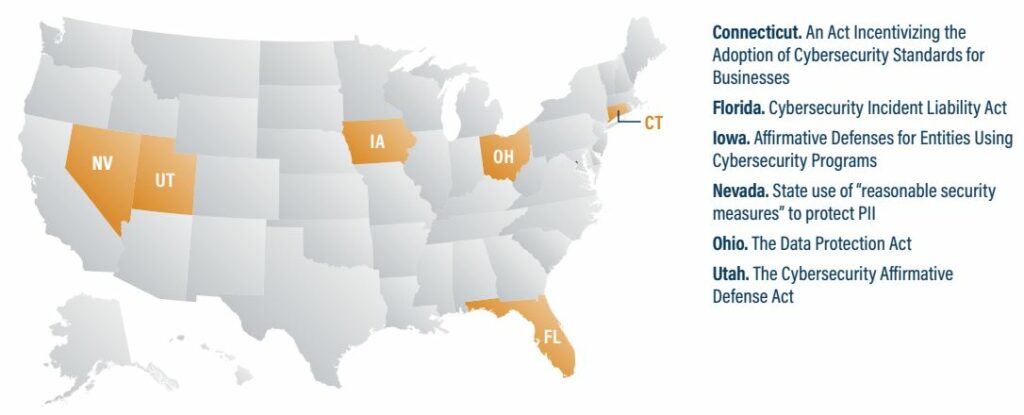
Center for Internet Security – A Guide to Defining Reasonable Cybersecurity
Furthermore, six states—Connecticut, Florida, Iowa, Nevada, Ohio, and Utah—have enacted laws defining reasonable cybersecurity through adherence to recognized frameworks such as the CIS Critical Security Controls, NIST standards, and ISO 27000 series. For example, Florida’s Cybersecurity Incident Liability Act incentivizes the adoption of these best practices by offering legal protection to organizations that implement them, ensuring that certain failures are not automatically deemed negligent.
Similarly, Ohio’s Data Protection Act provides an affirmative defense against lawsuits resulting from data breaches, encouraging businesses to follow established cybersecurity guidelines in order to mitigate legal risks.
While these state initiatives promote stronger cybersecurity practices, the absence of a unified federal definition results in confusion and inconsistency among businesses. Consequently, the level of protection varies significantly depending on the state, leaving some organizations more vulnerable than others.
Implementing Cybersecurity Safeguards
The CIS guide outlines a structured approach for implementing cybersecurity measures that include:
Knowing Your Environment
Maintaining an accurate inventory of all hardware and software assets ensures that high-value data is adequately protected. This step is foundational for prioritizing security efforts and minimizing attack surfaces. Organizations should actively manage all assets, including end-user devices, network devices, non-computing IoT devices, and servers, to accurately know the assets that need to be monitored and protected.
This inventory process supports identifying unauthorized and unmanaged assets, allowing for their removal or remediation. Additionally, it includes managing the security lifecycle of software and hardware to prevent vulnerabilities from being exploited.
Account and Configuration Management
Effective cybersecurity requires strict control over user accounts and system configurations. This includes defining the processes and rules for creating and revoking accounts and determining what access different users have to system resources.
Managing access is essential because compromising accounts is a very common attack vector. Applying and maintaining secure configurations across hardware and software assets is also critical. Automated patching and software updates, along with configuring the collection, aggregation, and review of audit logs, help detect and understand attacks.
Establishing secure configurations for network devices and enforcing automatic session locking are additional measures that can help mitigate risks.
Security Tools
Utilizing commercial cybersecurity tools can protect against common threats such as malware and phishing attacks. Continuous monitoring through tools like Endpoint Detection and Response (EDR) helps detect and respond to threats in real-time.
Organizations can deploy tools to prevent users from accessing malicious websites and block harmful email attachments. Host-based and network intrusion detection and prevention tools are also critical for defending against threats across the enterprise’s infrastructure and user base.
Data Recovery and Incident Response
Having detailed and specific data recovery processes, including regularly automated backups, ensures a safety net in case of any lost or stolen data. Organizations must implement a data recovery process addressing the scope of recovery activities and the security of backup data.
An incident response plan with clear roles and responsibilities is equally important for handling breaches, including identifying key personnel responsible for incident coordination, maintaining contact information for stakeholders, and conducting routine incident response exercises.
Regularly testing backup recovery and conducting post-incident reviews are essential for refining these processes and making sure that when a real cyberattack occurs, the recovery process is familiar and organized.
Security Awareness
An effective cybersecurity program involves educating employees about security best practices and conducting regular training to defend against social engineering attacks. This education is the most effective defense against attacks where threat actors impersonate trusted sources.
Regular security awareness training should cover recognizing phishing attempts, understanding authentication best practices, and proper handling of sensitive data. Training should extend to ensuring remote workers securely configure their home network infrastructure.
Organizations can also test the effectiveness of these efforts through penetration testing and vulnerability assessments.
Business Processes and Outsourcing
As businesses become increasingly interconnected, managing third-party risks has become critical, especially when external service providers handle sensitive data.
Organizations must develop processes to evaluate and manage the security practices of service providers responsible for their sensitive data and functions. This includes inventorying and classifying service providers, ensuring contracts include security requirements, and regularly assessing and monitoring provider compliance.
Effective service provider management mitigates risks associated with outsourcing and ensures that external partners uphold the organization’s cybersecurity standards.
While the CIS’s checklist is not a federal mandate, prioritizing the steps above can help businesses in any state be confident that they have gone above and beyond required efforts to implement “reasonable cybersecurity.” This proactive approach can help keep organizations free of hackers and away from any litigation problems with the government, ensuring a more secure and legally compliant operational framework.
Continuous Improvement and Monitoring
Implementing cybersecurity safeguards is not a one-time task but a continuous process that demands regular monitoring and refinement. Organizations are encouraged to conduct frequent cybersecurity assessments and audits to identify potential vulnerabilities and areas for improvement.
These assessments should include vulnerability scans and compliance audits to ensure that security measures are both effective and current.
In addition to creating an incident response plan, it has been described as crucial to regularly test and update this plan. This practice ensures that the organization remains prepared to handle security breaches effectively, adapting to technological advancements and the evolving tactics of threat actors.
By emphasizing continuous improvement and monitoring, organizations can significantly enhance their cybersecurity posture and reduce the risk of data breaches today, and in the foreseeable future. This proactive approach not only safeguards valuable assets but also ensures compliance with dynamic legal and regulatory requirements.
The Wrap
The cybersecurity compliance and best practices environment is quickly evolving, presenting both challenges and opportunities for business leaders today. The absence of a unified national standard for “reasonable cybersecurity” in the United States has created a complex web of state laws and industry-specific regulations. This fragmented approach leaves many organizations struggling to navigate the legal and operational aspects of cybersecurity implementation.
CIS’s “Reasonable Cybersecurity Guide” offers a valuable framework for organizations to address these challenges, ensuring that every business, regardless of location or regulatory landscape, is as prepared as possible. By following its approach, from understanding the virtual environment to implementing effective security tools and practices, businesses can enhance their protection against cyber threats and strengthen their legal position.
For business leaders, the key takeaway is clear: proactive, comprehensive, and adaptable cybersecurity measures are no longer optional but essential for operational resilience, legal compliance, and long-term business success in our interconnected economy.







